The experience of BBC Cyber correspondent Joe Tidy provides a rare and sobering look into the tactics used by major cyber-crime organizations to leverage employees for access. This incident perfectly demonstrates the dual threat of sophisticated Social Engineering combined with high-pressure Technical Attacks.
1. The Ransomware-as-a-Service (RaaS) Model
The criminal group behind the proposition, Medusa, operates a Ransomware-as-a-Service (RaaS) model. This means:
- Platform: Medusa’s administrators manage the core malicious software (the ransomware, C2 infrastructure) and recruit affiliates.
- Affiliate: The individual (“Syn”) who contacted Joe Tidy was a “reach out manager” acting as an affiliate. They use Medusa’s tools and platform to execute attacks.
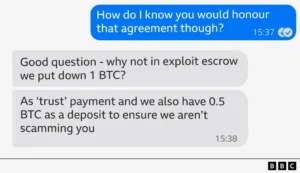
- The Incentive: The affiliate and the insider (Tidy, in this case) would share a significant cut of the final ransom payment, structured as a massive financial incentive to betray their employer (15% to 25% of a potential multi-million-dollar payout).
The fact that Medusa avoids targeting organizations in Russia and CIS states is a common characteristic of large, established RaaS operations, aimed at avoiding domestic law enforcement attention.
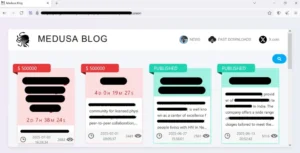
2. The Social Engineering Pitch
The attack began as a classic social engineering campaign, exploiting two key psychological factors: greed and dissatisfaction.
- The Lure: The immediate offer of “millions” and a beach house at the Bahamas targets greed, promising to eliminate the need to work again.
- The Discontent Hook: The hacker attempted to sow discontent by asking, “does the BBC actually pay you much at all,” seeking to frame the betrayal as a justified act against an underpaying employer.
- Trust and Proof: Tidy’s successful move to ask for proof forced the hacker to reveal operational details, including their darknet address and their recruitment process via a secure messaging service (Tox), lending credibility to their criminal operation and demonstrating commitment.

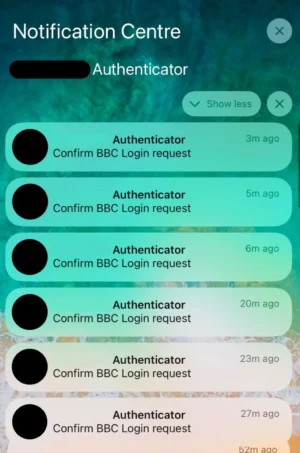
3. The Technical Escalation: MFA Bombing
After Tidy stalled for time, the attackers shifted from social engineering to a direct, high-pressure technical attack designed to force a mistake: Multi-Factor Authentication (MFA) Bombing, also known as MFA fatigue.
- The Mechanism: The attacker repeatedly attempts to log in using the victim’s known credentials (or simply the username/email), which triggers a continuous stream of push notifications or text messages asking the victim to confirm the login.
- The Goal: The aim is to overwhelm or annoy the victim to the point where they click the “Accept” or “Approve” button just to make the notifications stop. Once approved, the hacker gains full access to the account without needing the password.
- The Impact: As Tidy described, it took the conversation out of the chat app and directly onto his home screen, making the phone “unusable” and creating a feeling of aggressive physical intrusion (“aggressively knocking on my front door”).
This tactic is extremely effective because the MFA system itself is often trusted and designed to simply ask, “Was this you?” rather than flagging the request as malicious.
4. Mitigation and Defense
The BBC’s response—to immediately disconnect the employee entirely from all systems and fully lock the account—was the correct security protocol.
While Tidy did not have high-level IT access, an attacker gaining control of his account could still have used it for:
- Lateral Movement: Using the legitimate BBC account to navigate the internal network, find other systems, and identify privileged accounts.
- Phishing: Sending internal phishing emails to other employees from a trusted BBC email address.
- Intelligence Gathering: Stealing non-public data, source code, or internal communications.
The story serves as a critical reminder that security is not just about firewalls and antivirus; it is fundamentally about employee training, strong protocols, and the ability of security teams to respond to a fast-moving, high-pressure human attack.
Source: BBC